UK businesses continued to face extreme levels of cyberattack activity throughout 2025
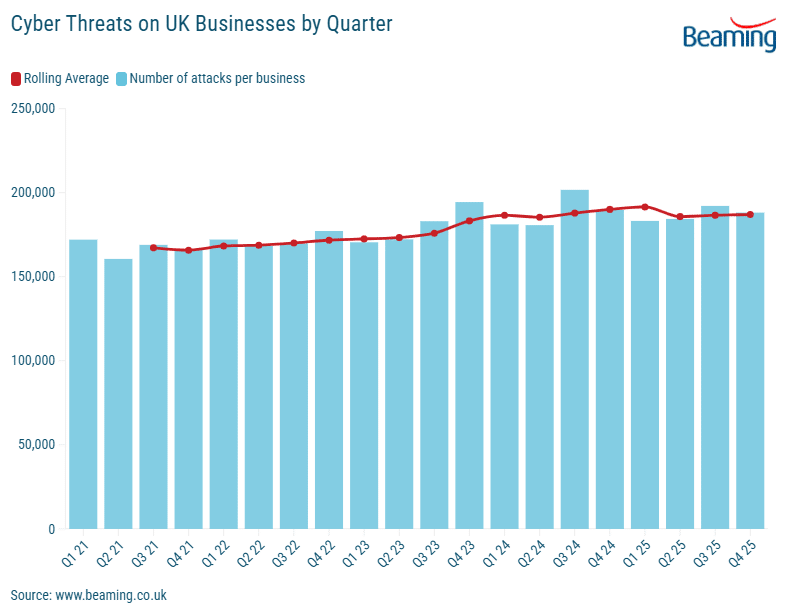
Beaming’s analysis of malicious traffic targeting UK businesses shows that 2025 remained one of the most hostile years on record, with companies experiencing an average of just over 2,000 cyberattacks per day. While this represents a slight easing from 2024’s peak, the overall picture is clear: elevated cyber risk is now the norm, not the exception.
Attackers continued to probe internet‑facing systems relentlessly, with sustained pressure on databases, remote access services, VPNs and web applications. The volume and persistence of this activity underline the need for UK organisations to maintain strong, layered defences and to prioritise resilience in their 2026 strategies.
The 2025 Cyber Threat Landscape
Across 2025, UK businesses were targeted an average of 791,600 times each. This constant probing was consistent throughout the year.
- Q1: 2,234 attacks per day
- Q2: 2,082 attacks per day
- Q3: 2,138 attacks per day
- Q4: 2,221 attacks per day
While these figures represent a slight stabilisation compared to the peak of 2024, 2025 still sits firmly within the top three most hostile years ever recorded by Beaming. The data suggests that attackers are no longer following seasonal patterns but are instead maintaining a high baseline of automated activity year-round.
2026 Priority: Build resilience, not just prevention
For 2026, businesses should prioritise automated, continuous monitoring. This includes maintaining immutable backups and regularly testing recovery processes to ensure the business can remain operational even if a breach occurs. Businesses also need to prepare for the UK Cyber Security and Resilience Bill, with this new legislation expected to take full effect in 2026, businesses must shift from periodic security checks to continuous compliance.
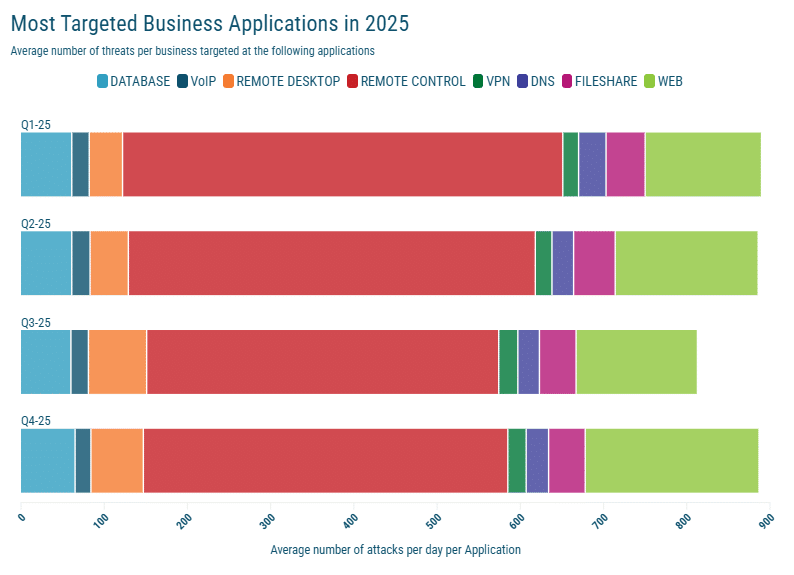
Where Criminals Focused Their Efforts
In 2025, attackers continued to target the services that keep UK businesses connected and operational.
- Databases: Systems remained a primary target. Attackers focused on misconfigured ports and outdated database engines to facilitate data theft and ransomware.
- Remote Desktop & Remote Control: RDP services saw persistent, high-volume probing. These remain a favourite entry point for ransomware groups seeking to hijack administrative access.
- VPNs & Remote Access Infrastructure: VPN services were targeted relentlessly, with spikes often coinciding with the disclosure of vulnerabilities in major VPN appliances.
- Web Applications & Filesharing: The second half of 2025 saw a rise in credential stuffing and automated vulnerability scanning against web-based collaboration tools.
2026 Priority: Reduce Your Attack Surface
Businesses must audit all internet-facing services. We recommend removing or restricting unnecessary ports and placing sensitive systems (such as databases) behind secure gateways. Implementing a Next Generation Firewalls and ensuring Multi-Factor Authentication (MFA) is enforced across every single remote login is non-negotiable for the coming year. As credentials remain a primary target, businesses should adopt identity-first security through conditional access policies. This approach ensures that access is granted based on more than just a password, factoring in critical context such as user location, device health, and the time of day.
Where Attacks Originated:
China remained the largest source of malicious traffic in 2025, frequently exceeding 30,000 unique attacking IP addresses per month. However, Beaming’s latest analysis reveals that the USA has significantly narrowed the gap, now following more closely as a major source of attack infrastructure than in previous years. These two nations, alongside Brazil, India, and Russia, constitute the top five origins of cyber threats reaching UK businesses.
Beaming notes that this threat landscape is increasingly global and industrialised. Rather than relying on short-lived infrastructure, attackers are utilising large, well-maintained botnets that allow for a sustained and relentless volume of probing.
2026 Priority: Intelligent Filtering and Geo-Policy
Traditional IP blacklisting is no longer sufficient. In 2026, where possible, organisations should restrict access from countries where they have no legitimate business interests to reduce the noise and risk. But also, IT leaders should implement behaviour-based threat detection that can identify malicious patterns regardless of the source IP.
2025 in Context: High-Profile Incidents
The trends observed in Beaming’s analysis were mirrored by several high-profile incidents that dominated the press in 2025.
- Manufacturing and Supply Chain: The ransomware attack on Jaguar Land Rover, which halted production and caused significant economic damage, highlighted the vulnerability of smart factories and the supply chain.
- Retail and Logistics: Major breaches at Marks & Spencer and the Co-op Group disrupted online orders and loyalty systems for weeks, exposing the data of millions of customers.
- Public Sector and AI: The NCSC reported a record number of “nationally significant” incidents. Furthermore, 2025 saw the rise of AI-driven fraud, including deepfake impersonations of executives to authorise fraudulent transfers.
2026 Priority: Review Supplier and Cloud Risk
As seen in the 2025 breaches, your security is only as strong as your weakest supplier. For 2026, IT leaders must assess the security controls of third-parties and prepare contingency plans for supplier outages. Verification processes must also evolve to protect against AI-enhanced social engineering.
Beaming’s Role in Protecting UK Businesses
As a specialist business ISP, Beaming uses this threat intelligence to strengthen network-level filtering and update intrusion prevention signatures in real time. We prioritise security in our network design to help keep our customers’ data safe.
Our goal is simple: to keep UK businesses connected and protected, as the cyber threat landscape continues to evolve.