Q2 2022 Cyber Threat Report
Corporate cyberattacks spiked in May but fell overall in Q2
- Average UK business experienced a cyberattack every 47 seconds between April and June
- Beaming’s analysts identified large numbers of attacking IP addresses in the USA, India and Taiwan
- Remote control, web and file sharing were the most frequently targeted applications
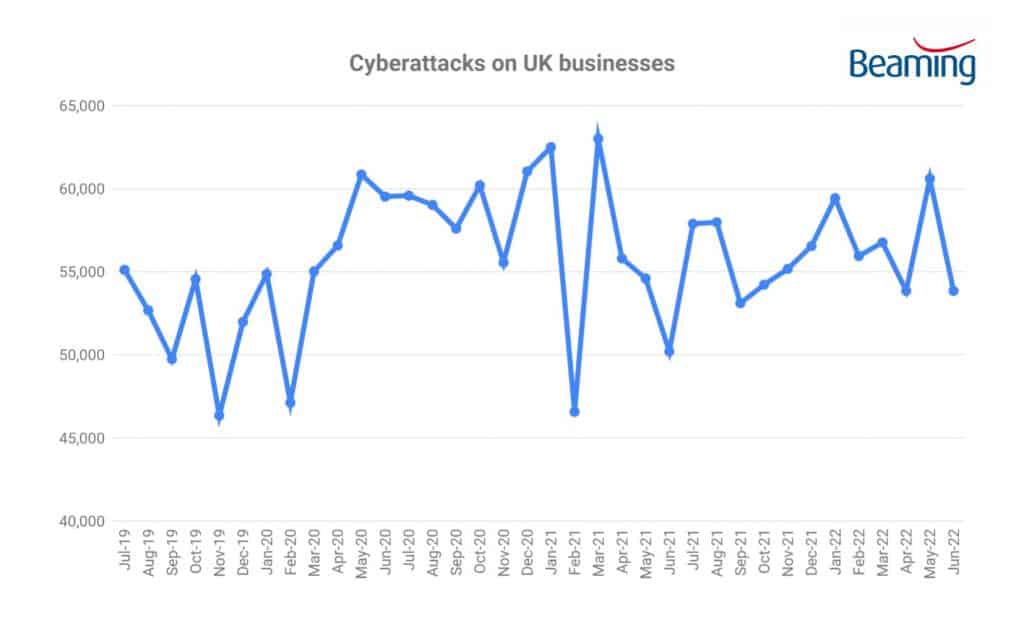
British businesses experienced 168,305 cyberattacks each in the second quarter of 2022. On average, companies experienced a new attempt to breach their firewalls every 47 seconds between April and June.
Beaming’s analysis reveals that, with 60,605 cyberattacks, May was the busiest month for malicious online activity experienced by businesses since March 2021. However, this spike occurred during a broader period of falling cyberattack activity, which declined by three per cent in the quarter.
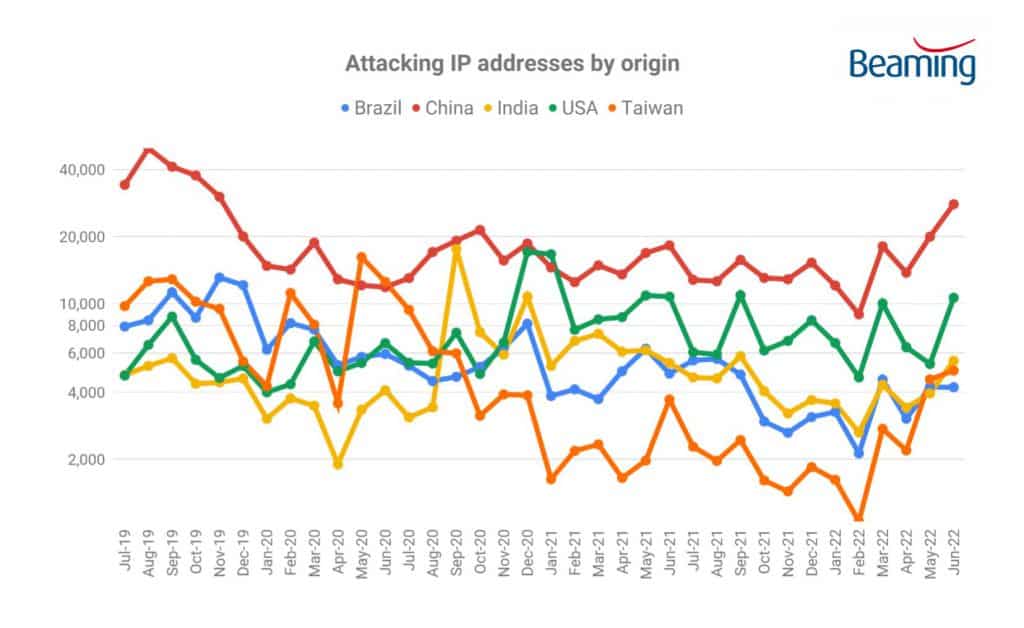
Beaming identified 309,499 IP addresses used to launch cyberattacks on UK businesses during the second quarter. Its analysts traced 61,786 cyberattacks to locations in China and also identified large numbers of attacking IP addresses in the USA (22,383), India (12,911) and Taiwan (11,776). Hackers targeted remotely controlled devices, web applications and file-sharing services most frequently.
Sonia Blizzard, managing director of Beaming, said:
“Although the volume of cyberattacks on UK businesses fell slightly during the second quarter of 2022, the threat remains high and constant. Malicious May was an important reminder that businesses of all sizes should be vigilant.”
“Company firewalls and IT systems remain under constant pressure. You should do so now if you haven’t reviewed your cybersecurity and intrusion detection measures in the last 12 months.”
Sign up for further insights
Be first to receive our cyber threat report and you’ll receive new statistics each quarter, before anyone else and with in depth analysis.