Q3 2022 Cyber Threat Report
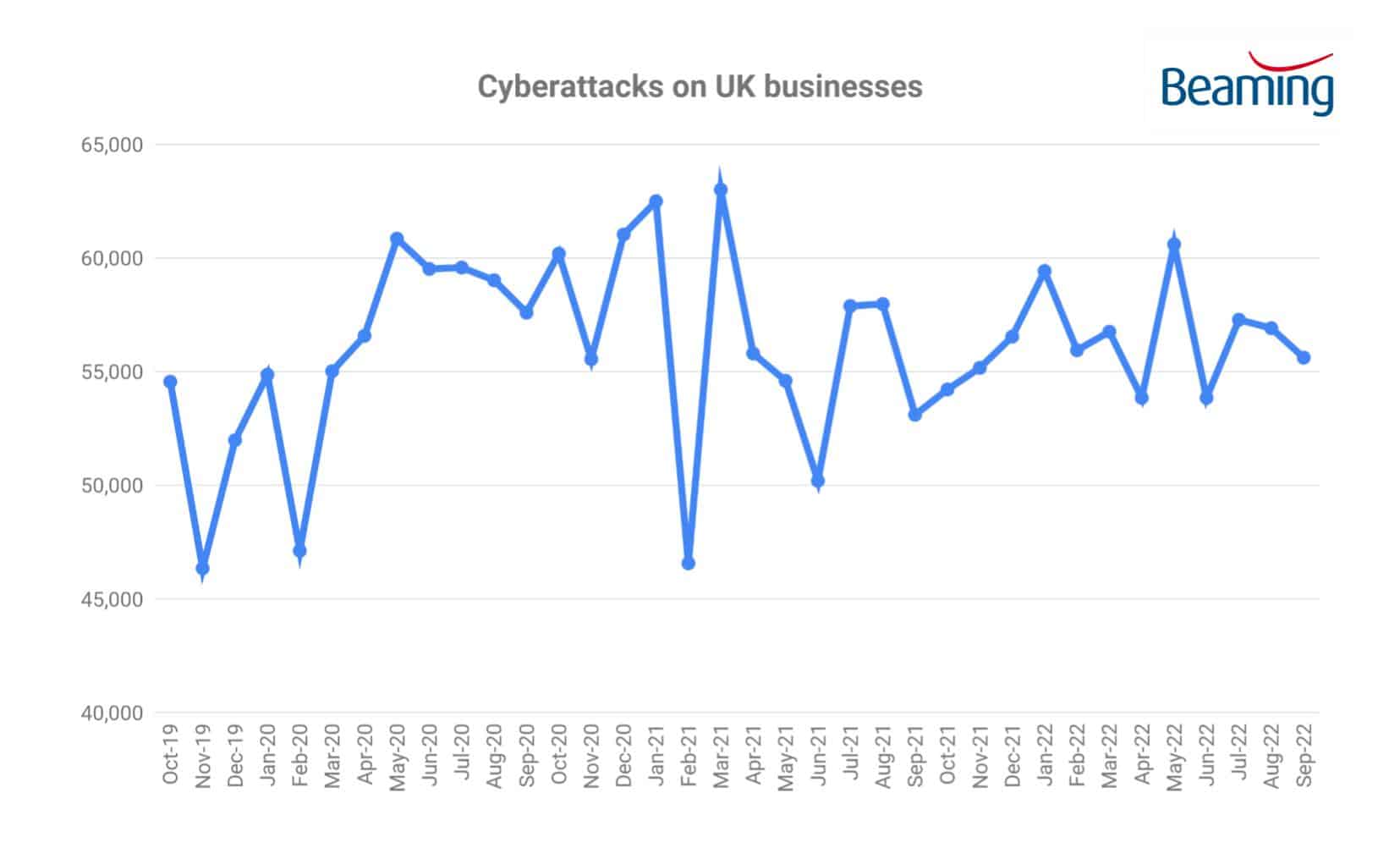
- Businesses experienced 169,824 cyber attacks between July and September
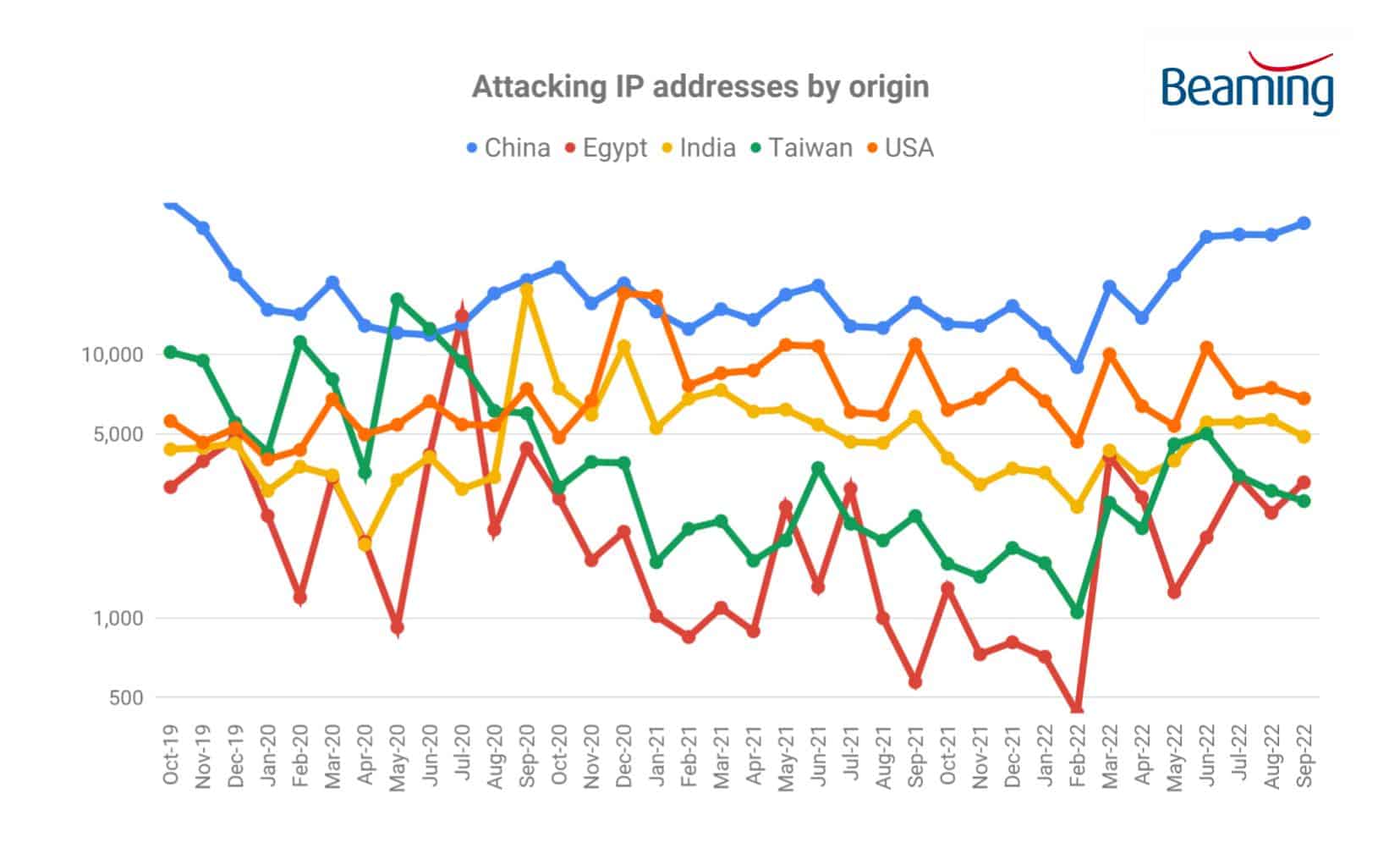
- More than a quarter of attacks were traced to locations in China
- Businesses investing in next generation firewalls and other measures to reduce risk
The volume of cyber attacks on UK businesses fell by four percent in the third quarter of 2022, but remains high by historical standards. UK firms experienced 169,824 attempts each to breach their systems between July and September, on average, the equivalent of one every 47 seconds.
Sonia Blizzard, managing director of Beaming, said: “Cyber attack levels leapt to an all time high when workers went home during Covid, and have remained elevated ever since. It’s encouraging to see attacks fall over the summer, but firms should continue to be vigilant.”
“Business leaders must ensure they are doing everything they can to avoid exposing their people, assets, customers and business partners to greater risk. We are seeing more businesses investing in next generation firewalls, unified threat management devices and intrusion detection systems to improve their online resilience.”
Beaming identified 341,750 IP addresses used to launch cyberattacks on UK businesses during the summer months. More than a quarter (88,625) of attacking addresses were traced to locations in China, and large numbers of attackers appeared to be located in the USA (21,449) and India (16,083).
The systems most frequently targeted by hackers included remote control services and networked devices, web applications and file-sharing services.
Sign up for cyber security insights
Be first to receive our cyber threat report and you’ll receive new statistics each quarter, before anyone else and with in depth analysis.