Protect data when an employee leaves
Posted on 20 February 2017 by Beaming SupportEmployees coming and going is a part of business and whether they go on good terms or not it is important to protect data when an employee leaves
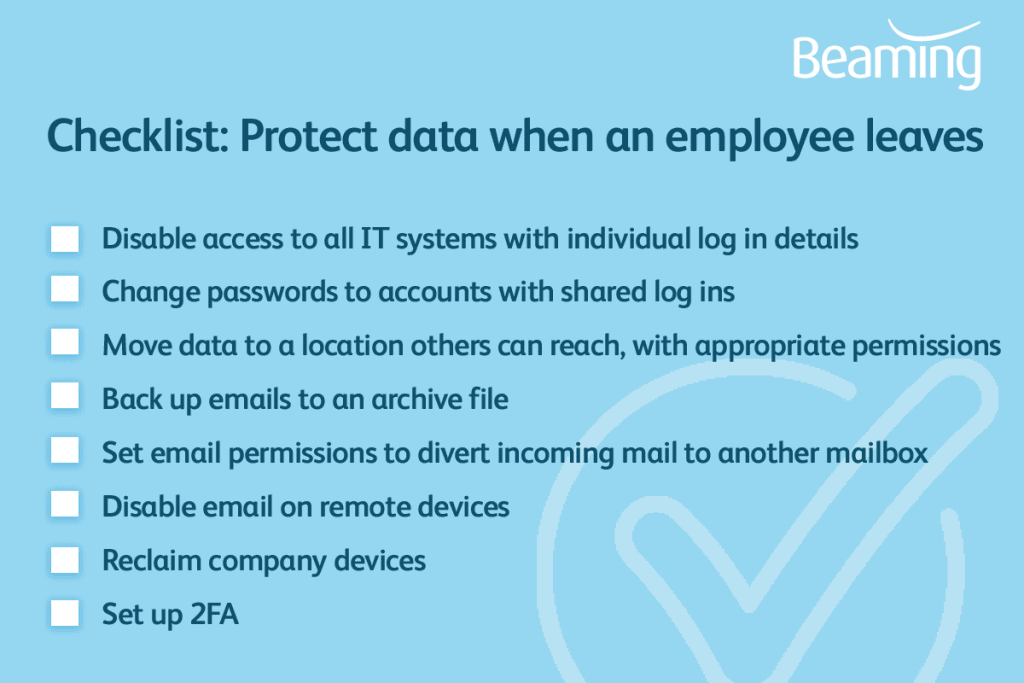
The first action when an employee leaves would be to disable access to IT systems, this will prevent anyone downloading or tampering with data. If access remains, an ex-employee, – or anyone they pass login details to – could compromise the data. Also original data could be lost if there is not a backup process in place.
If the employee had access to online accounts or cloud based software such as social media or analytics then you should change all passwords to prevent any deliberate or accidental mis-use. It would be good practice to regularly change passwords so only the agreed members of staff could log in to these accounts.
Employees might have built up a range of customer, supplier or product data which would still be useful to the company after they’ve left. In order to keep this data safe it can be moved to a location where it is available to the members of staff who will need it. If moved to a location on a shared drive on a server then the folder can have security permissions applied so that only certain members of staff can access the folder.
Emails can also hold vital information for business so it can be important that they are kept for a period of time. Emails can be backed up into an archive file and opened within another user’s email program or permissions can be applied for another user to open the leaving user’s mailbox within their own. If necessary it is also possible to apply permissions for another member of staff to email as if they are the ex-employee.
If the employee uses their own device to access emails, revoke access to that device. You can find instructions on how to prevent email access on a mobile device here. If you’ve issued them with their own mobile phone, tablet, laptop or any other equipment, make sure this is returned to you.
It’s good to have two factor authentication enabled anyway, and hopefully you do. If not, enable it on your important accounts now. That way, you should get an email notification if an unusual device tries to gain access.
These measures should protect data when an employee leaves so that it is available only to those who require it and is secured by the permissions put in place.
Need more guidance on cyber security?
Beaming’s Business Guide to Cyber Security will help you identify weak spots in your business and gives practical guidance on protecting against cyber attacks.