Configure an IPSEC VPN between two Cisco routers
Posted on 17 March 2013 by Beaming SupportWe want to configure an IPSEC VPN from site to site
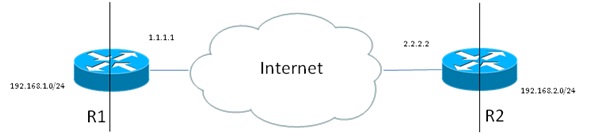
If you want to configure an IPSEC VPN from site to site, as per the below diagram, follow our guide.
To do this, there are 3 steps that we need to configure. These are:
- Configuring the traffic to be encrypted
- Configuring phase 1 of the IPSEC VPN
- Configuring phase 2 of the IPSEC VPN
Traffic to be encrypted
On R1:
Access-list 166 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
On R2:
Access-list 166 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
Configure IKE phase 1
This phase establishes a Security association between the two routers.
On R1:
crypto isakmp policy 100 encr 3des hash md5 authentication pre-share group 2
On R2:
crypto isakmp policy 100 encr 3des hash md5 authentication pre-share group 2
Configuring Phase 2
It is during this phase that the IPSEC tunnel is actually established
On R1:
crypto isakmp key A_PASSWORD address 2.2.2.2 ! crypto isakmp keepalive 300 ! ! crypto ipsec transform-set TransName esp-3des esp-md5-hmac ! crypto map CRYPTO 10 ipsec-isakmp set peer 2.2.2.2 set transform-set TransName match address 166 ! interface Dialer 1 Crypto map CRYPTO
On R2:
crypto isakmp key A_PASSWORD address 1.1.1.1 ! crypto isakmp keepalive 300 ! ! crypto ipsec transform-set TransName esp-3des esp-md5-hmac ! crypto map CRYPTO 10 ipsec-isakmp set peer 1.1.1.1 set transform-set TransName match address 166 ! interface Dialer 1 Crypto map CRYPTO
Finally the chances are that you will have some sort of NAT between you and the end point. We need to stop the traffic that will be encrypted being NAT’d :
Assume your NAT is configured as such:
ip nat inside source list 175 interface Dialer1 overload
Then the configuration will be as below.
On R1:
access-list 175 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255 access-list 175 permit ip any any
On R2:
access-list 175 deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255 access-list 175 permit ip any any
We're networking experts
When it comes to private wide area networks and business continuity services, a “set it and leave it” approach just doesn’t cut the mustard.
Avoid internet downtime
Download the report to understand the landscape of potential internet downtime, and find strategies to reduce the risk of failure and mitigate disruption and financial impact when it does occur.